Product Offerings
One platform for comprehensive risk identification and assessments
Cloud Attack Surface Intel
Hundreds of attack surface feed intel across public clouds and through threat research aggregated for security scans
vFeed Correlated Threat Intelligence
Thousands of Correlated Threat Vulnerability Intel across standards, DBs, OS, CPEs, advisories, patches, packages, detections, exploits, etc.

Features
Contextualized Security
Security scanning engines correlate attack graphs from discovered resources to identify weak authn, privileges, misconfigurations, vulnerabilities, exfiltrations, insider threats, etc.
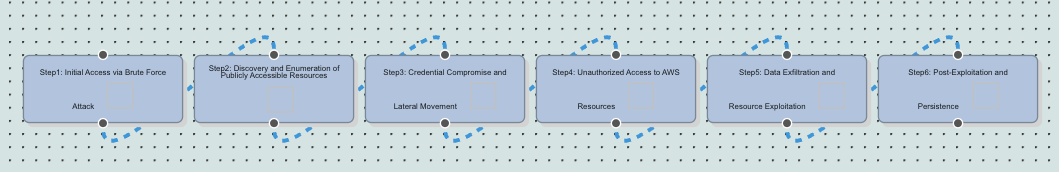
Attack Graph Playbooks
Build attack graph scenarios looking for attribute that demonstrate weaknesses
Dependency Graphs
Visualize entities and relationships among discovered resource
Discovery Agents
Discover resources using cloud service APIs
Enrichment
Agents build enriching nodes with metadata from cloud services.
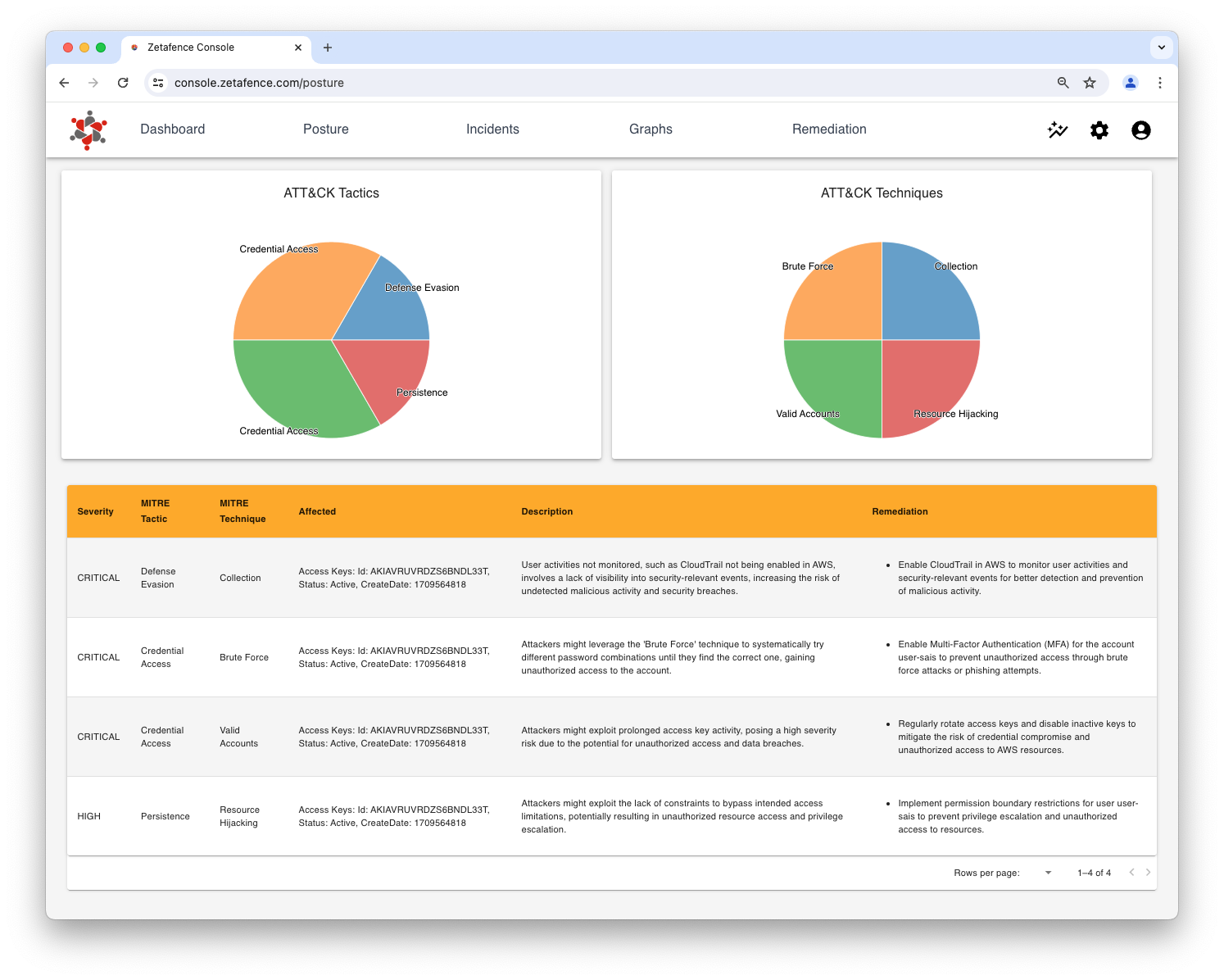
Posture
Continuous evaluation of security posture to identify MITRE ATT&CK TTM
vFeed Correlated Vuln Feed Intel
1000s of CVE, CPE, and cloud vulnerability feeds aggregated
Risk Scoring System
Risk Scoring using Accessibility, Privilege Levels, Sensitivity, Severity